Updated on: March 2, 2020
In today’s world, organizations are heavily dependent on information technology. It is necessary for them to protect their IT assets. Vulnerability assessment scan networks for known security issues and weaknesses. Someone who is malicious or we can say an attacker perform vulnerability assessment to find security weaknesses in the organizations network, computers and communication system so they can perform the attack to compromise the organization network to steal the valuable information.
On the other side, Vulnerability assessment plays an important role to provide security for an organization’s infra and resources from different kind of internal and external security threats. To secure the resources, an administrator need to perform patch management, deploy antivirus, firewall, check configuration issues in applications and hardware configuration.
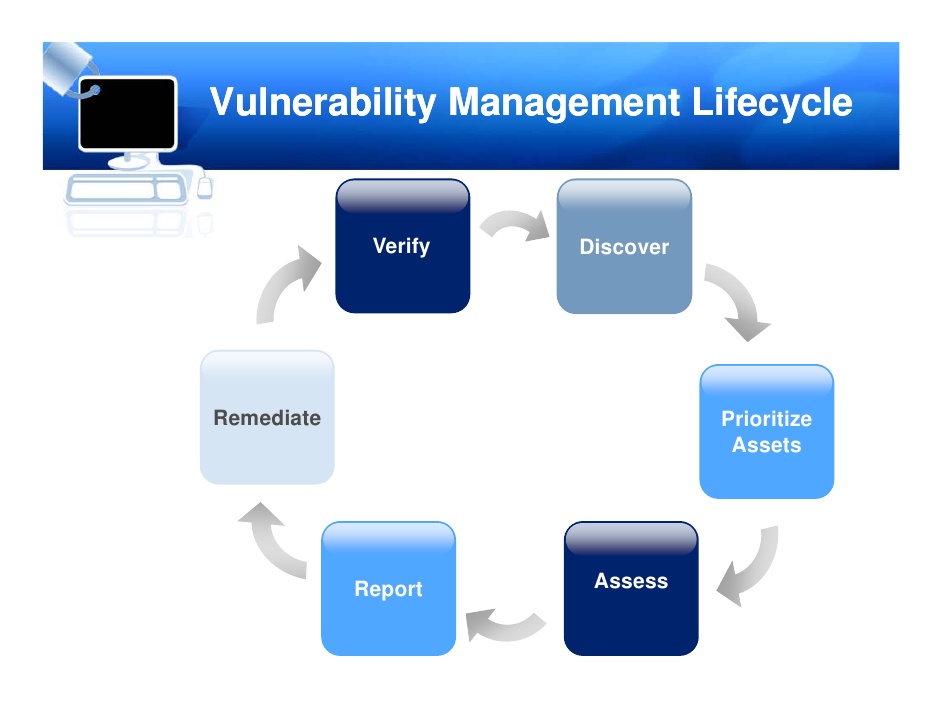
Vulnerability Management Life Cycle:
This is process that helps to finding and remediating security weakness before any attack.
Creating Baseline:
In this phase, Critical assets are identified and prioritized to define vulnerability management scope, define the policy and standards and define information protection procedure.
There is a list of things that you need to follow:
- Identify business process.
- Identify services, application, and data.
- Create a list of all assets.
- Prioritize the critical assets.
- Create Network infrastructure’s map.
- Identify previous control systems.
- Identify policy and standards.
- Define the assessment scope and create information protection procedures.
Vulnerability Assessment:
In this phase, Vulnerability scan will be performed to identifying vulnerability in the OS, web application, webserver, and other services. This phase helps to identify the category and criticality of Vulnerability and minimizes the level of risk.
Vulnerability Assessment Tasks:
- Examine and evaluate current physical Security .
- Identify miss-configuration.
- Identify Human errors.
- Perform vulnerability scanning through a tool.
- Prioritize the vulnerabilities.
- Validate the vulnerabilities.
- Create Vulnerability report.
Risk Assessment:
In this phase risk are identified, characterized and classified with risk control techniques. Vulnerabilities are categorize based on impact level (like Low, Medium, High).
Remediation:
Its refer to perform the steps that use to mitigate the founded vulnerabilities according to impact level. In this phase response team design mitigation process to cover vulnerabilities.
Remediation tasks:
- Prioritize recommendations
- Design a action plan to execute the recommendations
- Perform Root cause analysis
- Apply the solutions
Verification:
This phase help to verify all the previous phases are properly employed or not and also perform the verification of remedies
Task perform in this phase:
- Run Dynamic analysis
- Attack Surface verification
Monitor:
Incident monitoring is performed using firewall, IDS/IPS or SIEM tools.
Enroll for the VMware Training in Hyderabad





